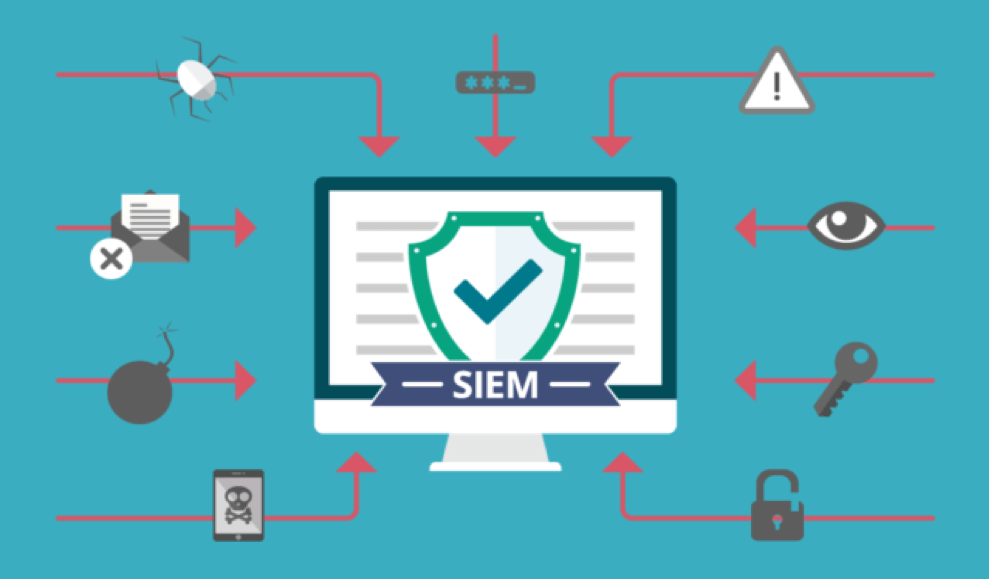
Despite the wide range of security tools at their disposal, organizations are increasingly using SIEM, a more complex and sophisticated piece of software, to monitor and protect their networks. The goal of providing a single place for all security-related procedures is known as “security information and event management,” or SIEM. A few examples of these actions include changes to log data, system configuration, and network activity. Employing a SIEM system enables businesses to quickly recognize and react to emerging threats, giving them an advantage in their efforts to prevent minor events from developing into significant catastrophes.
One of the most prosperous companies in the industry and a top provider of SIEM services is NetWitness. Their program will check all of the logs and packets in the system that your business uses. Even if someone can determine if they are accessing your computer maliciously, you can still tell. You will learn what makes them unique from the competition after interacting with one of their SIEM professionals.
SIEM Explanation
The terms “security information management” (SIM) and “security event management” (SEM), both of which come within the scope of the information technology industry, are combined to produce the acronym “SIEM.” SIM is able to gather information from a variety of sources and include it all into a single database, where it is then structured, standardized, and protected in preparation for in-depth analysis. This ensures that information is gathered consistently.
SEM employs rule-based algorithms to search the gathered data for any hidden instances of possibly harmful or suspicious activity. Data collection is necessary for this project. Monitoring user activity, such as login, file access, and transaction execution, is only one of the many things that can be done with SIEM. As a consequence, businesses get assistance in recognizing possible safety problems and implementing preventive actions. SIEM solutions are necessary for businesses and other organizations to efficiently monitor their cybersecurity and prevent major issues like hackers and data breaches.
SIEM Security Measures
As was previously said, security information and event management are referred to as SIEM. Businesses employ this cutting-edge technology to help manage and safeguard their internal networks. It acts as a central repository for all security-related operations, such as network activity, data logging, and configuration changes to the system. With the help of SIEM, businesses may learn all there is to know about their potential dangers and decide how to handle them as they arise, helping them to avoid terrible outcomes.
It is possible to have a better understanding of how a company’s systems and networks normally perform by using SIEM, which is used in enterprises. As a consequence, they may detect abnormalities that can point to wrongdoing or improper circumstances. Businesses may use SIEM as a tool to spot potentially dangerous behaviors in advance, pinpoint the source of the threat, and implement preventive steps to limit the harm.
In addition to decreasing the risks it presents, using a SIEM may make it easy to comply with industry regulations like HIPAA and PCI DSS. Businesses may simply audit their own systems with the help of SIEM to make sure they adhere to regulatory requirements. This is possible because it acts as a consolidated archive for all occurrences relating to system security. The SIEM is used to do this.
An increase in general security is the main benefit that SIEM offers enterprises. This is accomplished through enhancing network and system accessibility, improving the speed and accuracy of threat detection, and sustaining industry standards. If businesses have implemented the appropriate SIEM solutions, they may feel confident knowing that their data is safeguarded from those who would damage them. They are thus better able to focus on the main goals of their company.
The Benefits of Utilizing a SIEM
Businesses and other organizations may enhance their overall security posture in a number of ways with the help of SIEM systems. SIEM, sometimes referred to as security information and event management, has the power to provide insight into the whole network ecosystem. This has the immediate effect of increasing the visibility of potentially dangerous network behaviors and vulnerabilities before they have a chance to damage users. It may also be useful in identifying the dangers presented by adversarial insiders and other potentially dangerous persons who desire to get confidential information. If the data are correctly examined, this may very well be the case.
Researchers would find it much easier to identify possibly suspicious behaviors and take the necessary action if they used a SIEM system that can automate the examination of data from several sources. Response periods in the event of a security breach may be significantly shortened with the help of a properly constructed SIEM system that can carry out monitoring and alerting in real-time. Since a SIEM system offers a more in-depth understanding of the security posture of a particular business, it has the potential to significantly minimize the risk that a corporation is exposed to.
Security Software and SIEM
A company’s SIEM system may gather data from a range of sources, including firewalls, antivirus software, intrusion defense systems, authentication procedures, and network devices, in addition to other potential data suppliers. Other apps that relate to security may also provide data. The given data is subsequently checked for any relevant security flaws.
A SIEM system’s three main components are incident response, security analytics, and log management. The data that will be used in subsequent studies is collected from a variety of sources and stored in a centralized repository using log management. The security analytics module scans the incoming logs for repeating trends that can indicate unethical behavior or policy breaches. Last but not least, the incident response component speeds up the process of correcting problems by notifying people of potentially dangerous behaviors and providing remedies. This is useful while responding to circumstances.
Choosing the Best Possibilities
There are many alternatives available to you when selecting a cyber security firm to keep you secure online, but all of those other companies vary greatly from NetWitness. For the last 25 years, NetWitness has worked hard to establish a strong reputation as a reliable cybersecurity company that assists customers in safeguarding the privacy of their data using a variety of cutting-edge methods. Customers have profited directly from the service as a result of the company’s decades-long efforts to provide it.
A broad range of services is available from NetWitness. Some of these services include openness and transparency, analysis of user behavior data, and integrated threat intelligence. These services, which are offered while remaining one step ahead of the curve, allow customers and analysts to both stay one step ahead of any possible cyber hazards.
In addition to being able to give you the appropriate SIEM software, NetWitness is also equipped to provide you with the maintenance and support necessary to keep the program functioning properly and to help you with any issues that may crop up. To learn more about all the choices available to you and your business, visit the NetWitness website. After a hard day at work, you will be able to relax and unwind, knowing that your data is secure thanks to NetWitness’ assistance.